As cyber threats grow more complex, knowing the difference between MSP (Managed Service Provider), MSSP (Managed Security Service Provider), and MDR (Managed Detection and Response) is crucial, especially across specialist sectors like healthcare, legal, insurance, and government.The U.S. managed services market is projected to reach $69.6 billion by 2025, driven by increasing demand for outsourced […]
DNS often goes under the radar, works quietly in the background, keeping emails and apps running. But it’s quickly becoming one of the easiest ways for attackers to slip past your defenses. If you’re not watching DNS closely, you’re handing adversaries a hidden path into your network.As reported by CybersecurityNews, cybercriminals are using DNS TXT […]
For managed service providers (MSPs), cybersecurity isn´t just about securing devices anymore. Today, it also means spotting advanced threats, responding quickly, and staying compliant with changing regulations. Artificial intelligence is now a core enabler of these capabilities, delivering tangible benefits in both proactive threat intelligence and automated compliance management.Enhanced Threat Detection Through AIAI dramatically improves […]
Multi-factor authentication (MFA) was once seen as one of the best ways to protect accounts. Now, it’s a new entry point for attackers. In what’s called an MFA fatigue attack, hackers send repeated login requests hoping someone will get tired and just hit “Approve.” This tactic is now being used to bypass authentication in healthcare […]
In recent months according to Inc.com, U.S. organizations have seen a marked rise in politically driven cyber activity targeting networks, websites, and endpoints. From low-level defacement campaigns to more deliberate intrusions aimed at persistence and control, these attacks are increasingly tied to foreign-aligned actors responding to geopolitical developments. While some are opportunistic, meant to disrupt […]
On June 20, 2025, cybersecurity researchers revealed something that should concern every business and individual online: more than 16 billion login credentials have been exposed in a single data set. This isn’t a case of one major platform being compromised. The credentials span Apple, Google, Meta, Telegram, GitHub, government portals, and many others. As first […]
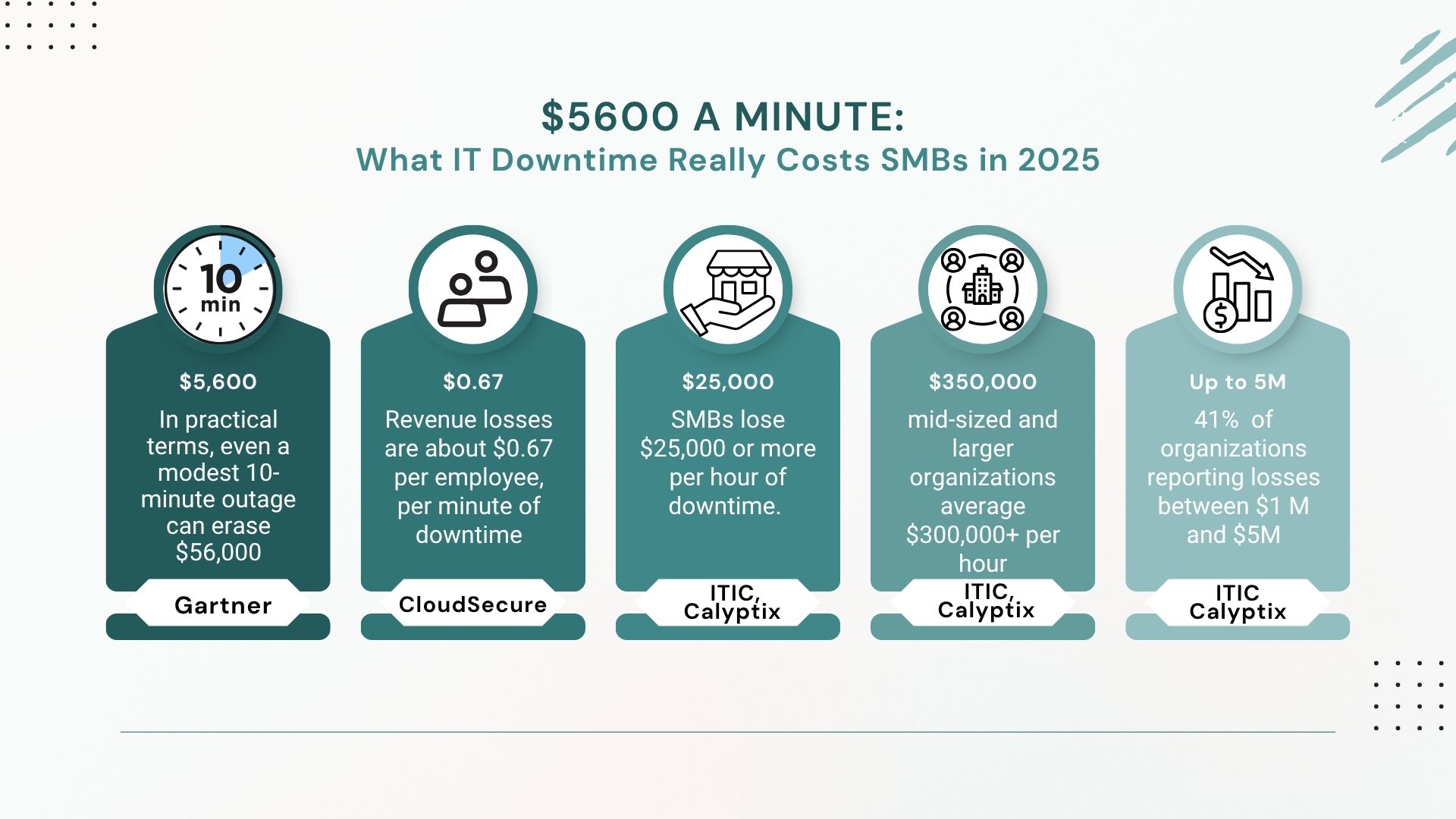
IT downtime is a direct financial threat. From missed revenue to operational chaos, even brief outages can cost small and midsize businesses thousands. Recent data shows just how sharp those losses can be. According to CatchMark’s late-2024 analysis, citing Gartner, the average cost of IT downtime is $5,600 per minute. In practical terms, even a […]
There’s a quiet but powerful shift happening behind the scenes of most modern businesses. While many companies are busy focusing on growth, innovation, and daily operations, a layer of technology is working in the background to keep everything running smoothly. This is where Remote Monitoring and Management, or RMM, comes in. It plays a big […]
In the past, managed IT services were mainly about fixing problems and cutting costs. Now, they’re becoming key partners in helping businesses grow and stay secure. Over the next five years, this role will continue to evolve, focusing more on preventing issues before they happen.This shift from reacting to problems to planning ahead is already […]
As more organizations adopt multi-cloud strategies to boost flexibility and avoid vendor lock-in, many are running into unexpected complexity. From disconnected tools and security blind spots to rising costs and unclear ownership, managing multi-cloud environments has become a growing challenge for IT teams.At Systech, we work closely with companies to bring structure, visibility, and security […]